
Important: this blog is for anyone to enjoy, that said you should not attempt to follow the steps if you don't have a solid grounding in Javascript, jsNode and code obfuscation.
“Don’t you just hate being infested with rats?” No longer an antiquated phrase fit for the 19th century. RATs, or Remote Access Trojans, are a malicious form of zombie malware that sits on your computer quietly waiting for the moment you input sensitive details such as passwords for your email accounts, logins to internet banking and more. These Trojans can tap your microphone, webcam and run scripts in the background without your knowledge. They have been such a severe issue that the recent RAT activity has been making the mainstream news as many victims have had their details stolen, resulting in material theft.
In this tutorial I am going to walk through how we can reverse engineer a recent javascript RAT virus to pick apart the javascript to extract the decoded contents of the malicious binary. This will allow you, and others to perform a proper and thorough analysis - which is critical for understanding how these viruses are manufactured, the mindset of the attacker and to better model future attacks to develop better defences. That said, lets get this out the way
Sir Common Sense
The malicious code has been distributed via email with a link that downloaded the script in the hopes someone would click and run the executable bringing them into a whole world of pain. Why would anyone do this? Well the executable was masked as an image file such as IMG-0001 where there could be a description such as ‘Dave was so crazy on his night out, check how wasted he got here’. It is very easy to complete child's play to trap a few victims when the email was disseminated to tens of thousands of users.
Downloading and Skimming the Code
STOP! Do not proceed to download unless you know what you are doing! Read the primer at the top if you are not sure. The sample virus code can be found here:
https://www.hybrid-analysis.com/sample/cd634825891a6813ce2878b878143e6799912c5e7c8d766faa49ef5e2f1ab07e?environmentId=100
First off lets rename file to netwire.js because that is the name of the malware that it drops. You will want to view this in a good code editor, sublime may crash when you try to save as a .js file or change the syntax to js. I recommend Atom for those with a slower computer. First lets have an eyeball of the code and you will notice right off the bat a big long variable being defined.
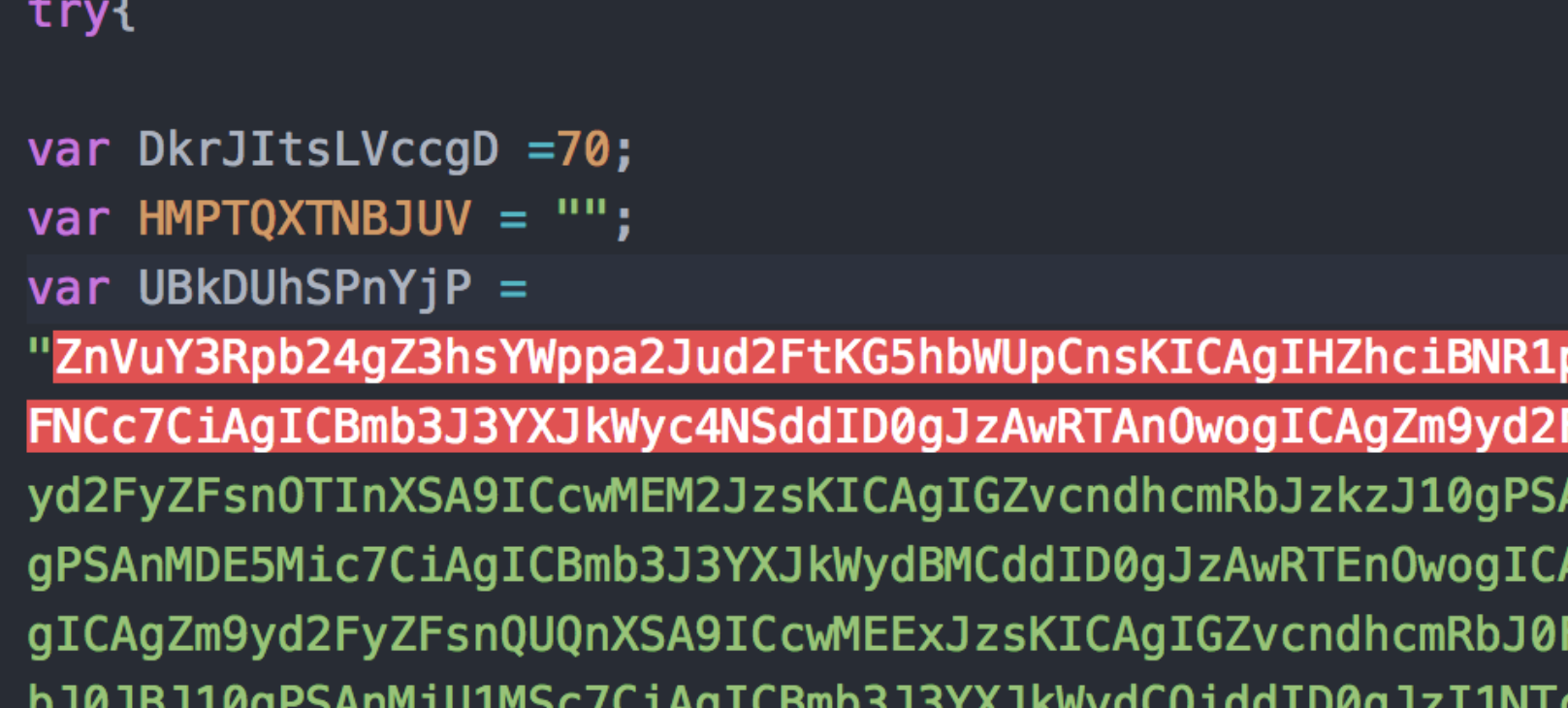
This variable has over 10,000 characters of code, and is a fair to say it likely has the contents of the malicious binary encoded into it and will have some kind of decoding routine going on at run time to drop the executables to disk.
Spotting the Deploy Function
Our job is to decipher the code to find out whats going on. If we look at the code below the variable we notice the following.
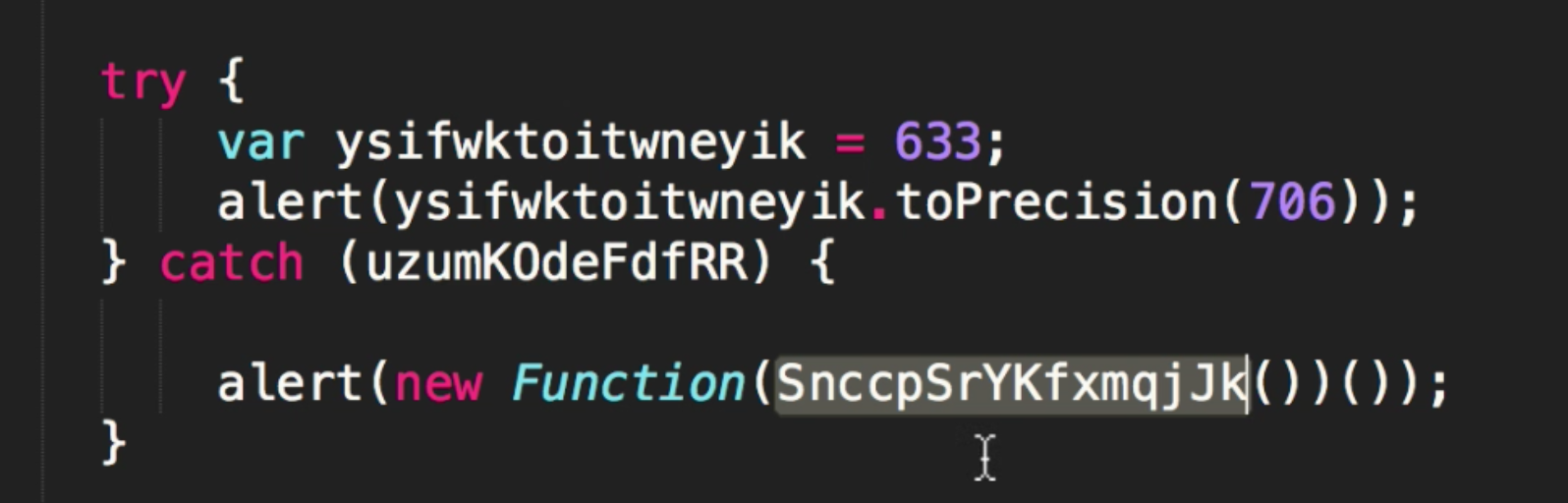
This is essentially trying to create an exception that it will catch, and then invoking the following function below it. The catch may be another way of throwing anti-virus software off the scent, as it only executes the function if the main criteria is not fulfilled.
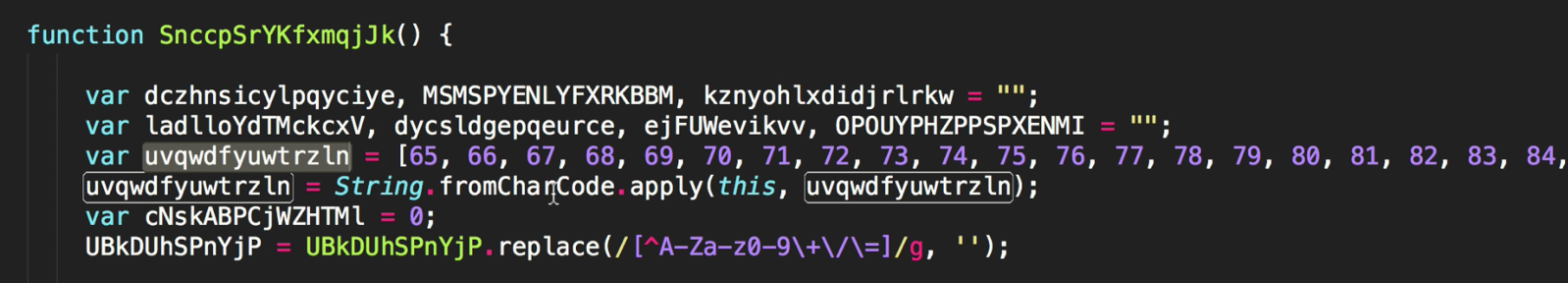
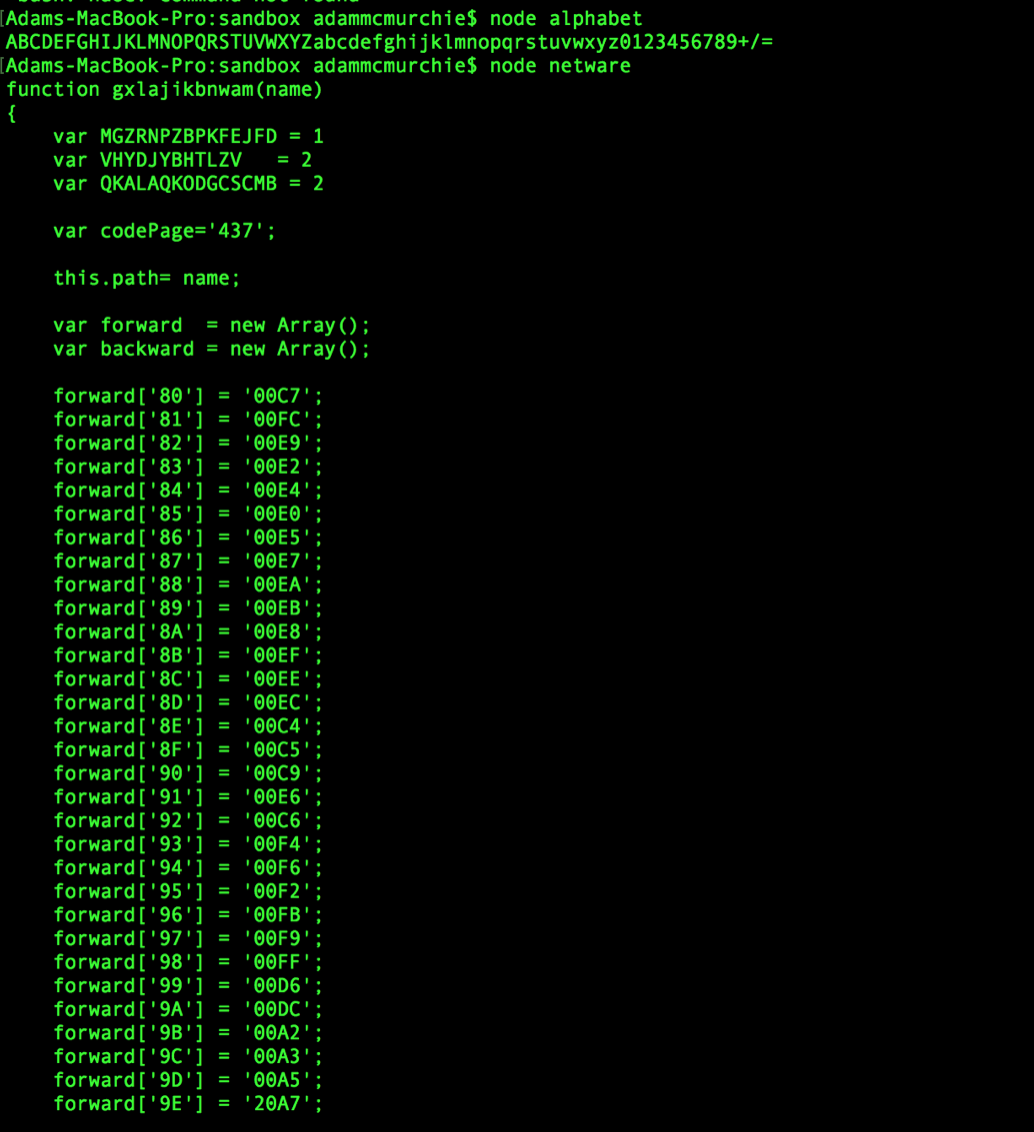
It has some variables being defined, and what looks like an alphabet. If you know your ASCII then you will know that 65 = A 66 = B 67 = C etc, so we have an alphabet being declared in an array. The next line is converting the array into a string. We can validate our assumption by cutting the following code snippet:
var uvqwdfyuwtrzln = [65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118,119,120,121,122,48,49,50,51,52,53,54,55,56,57,43,47,61];
uvqwdfyuwtrzln = String.fromCharCode.apply(this, uvqwdfyuwtrzln);Now lets append the following directly below (you will need jnode installed) and save it in a new file for example sample.js.
console.log(uvqwdfyuwtrzln)Now lets execute our sample.js in the terminal window by running node sample and we should see the following in the terminal output.
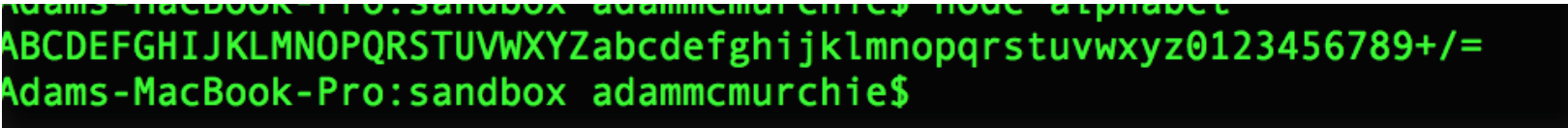
This is actually a base64, we know this as the string is in order of capitals then lower case, followed by 0 to 9, + and the =. This is essentially what defines the base64 alphabet. So we have a base64 encoded string to hide the true content.
Homing in on the Cleaning Function
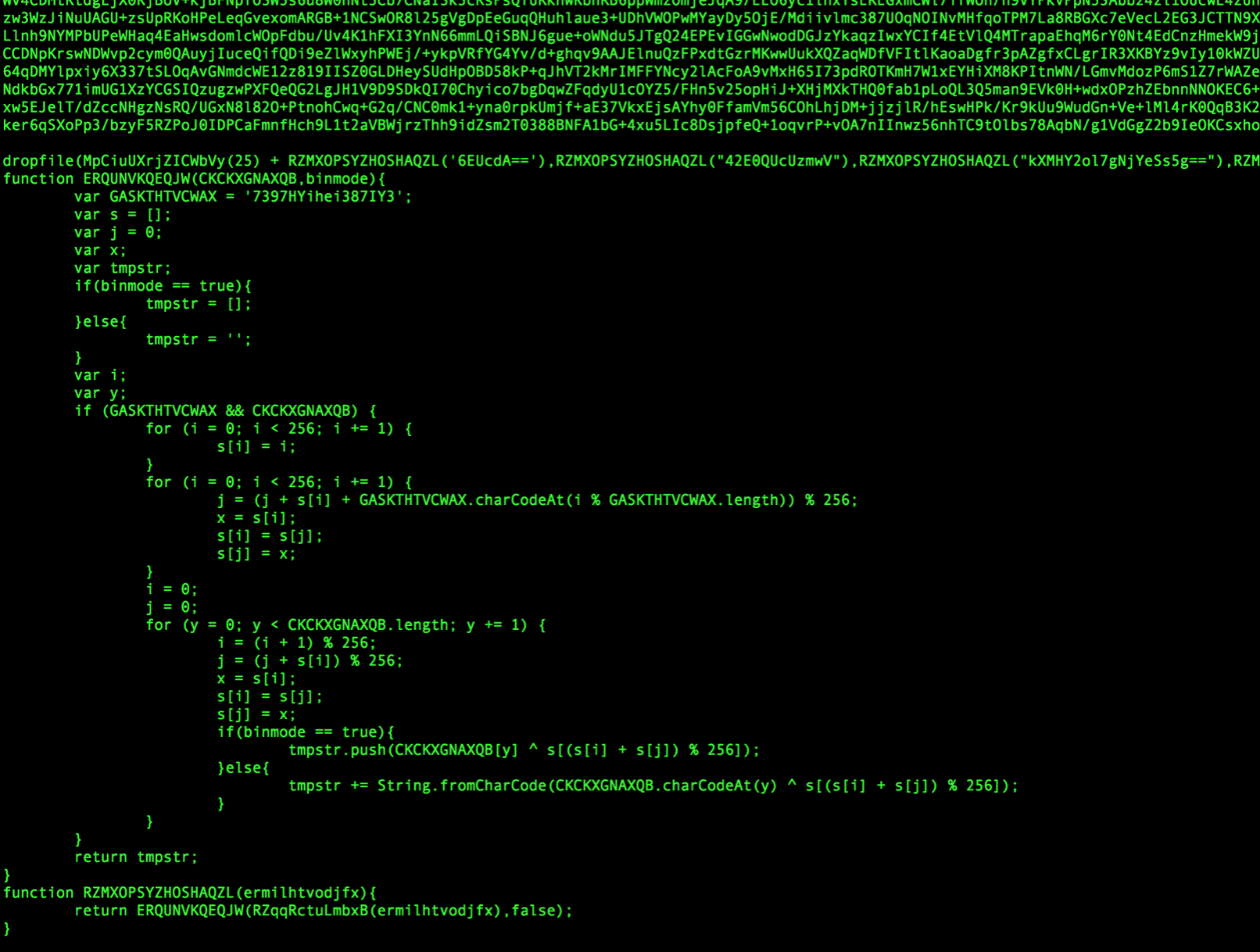
After the alphabet definition we see a regular expression replacement routine, and the string being manipulated is our big string.
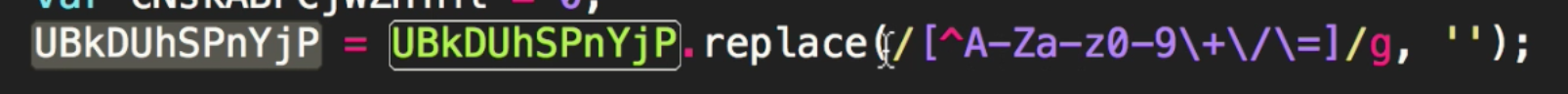
Have a look at the function replace, specifically after the carrot symbol, then look at what is being replaced….
Essentially it will take anything that does not equal the alphabet, then replace it with nothing. So this method basically cleans the big string into a base64 code that is valid. This suggests is once that occurs what we have left in the code below is just the decoding routine for the B64 string.
This is really easy to do something with, yay!
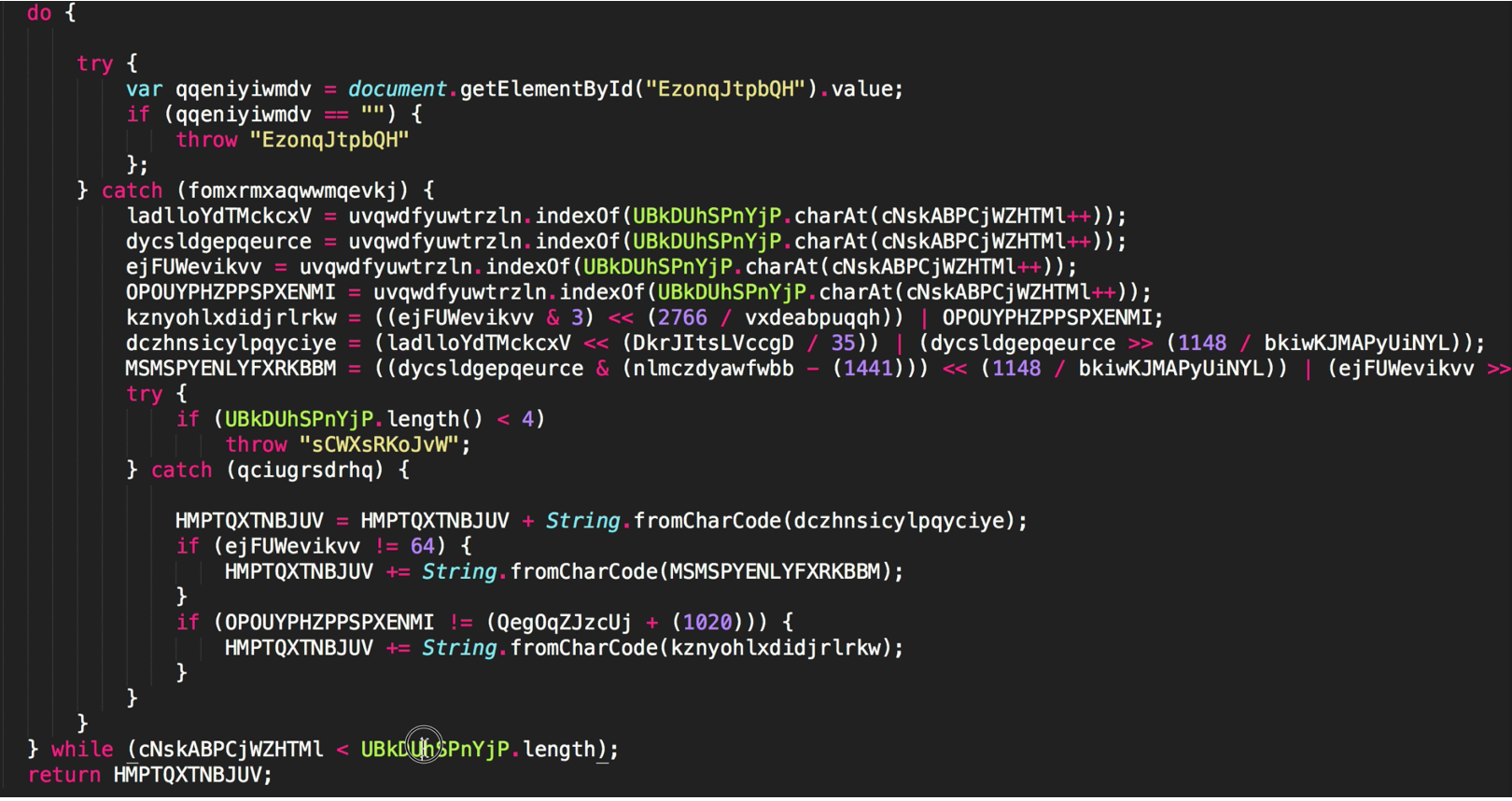
If we notice there is a do-while loop which is not used much in javascript these days, the bad guys may have thought this would throw others off their scent. It looks like this will iterate through the big chunk of encrypted data but we don’t need to worry about the specifics just now. The return value is the most important thing, and rather than returning the value, lets comment it out and add console.log for the variable and run it in node to see what is being returned.
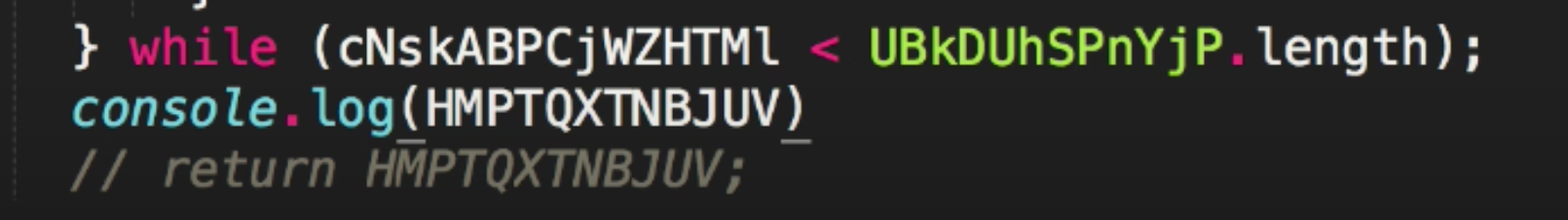
Now if we run this, we can see that nothing happens
That is because in this instance we have a try catch block (near the top) and even in the catch block there will be an error thrown, which wont show up as it is an alert and jsnode does not support this . So we need to get rid of that and invoke the method manually.
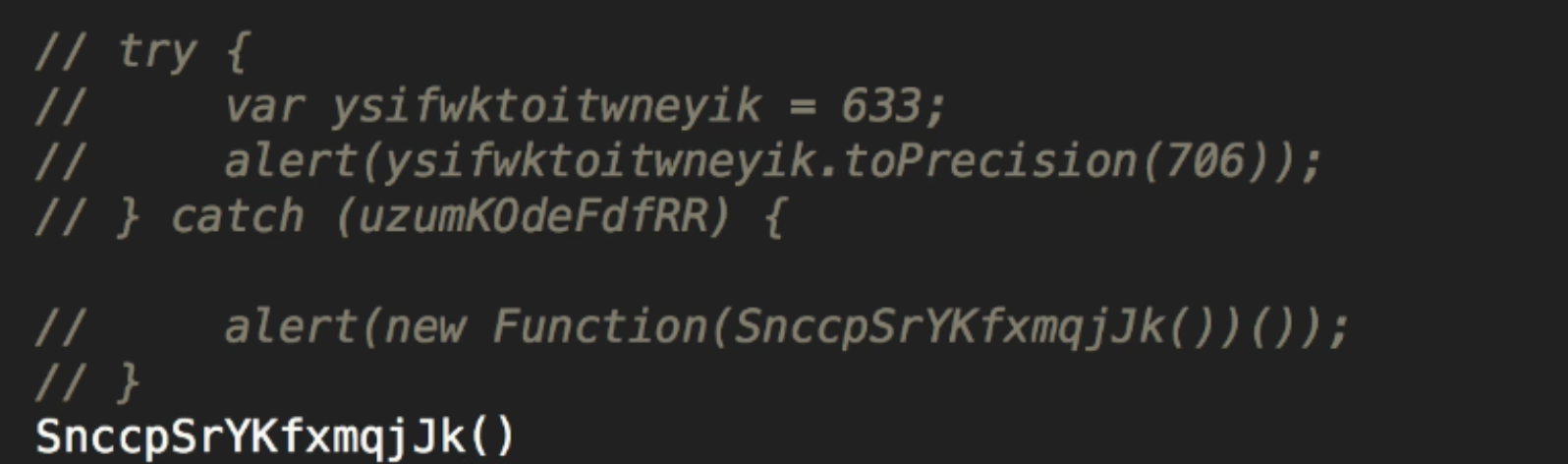
Now run this in node again with the command node file name and you will get the spectacular output as below.
Lets redirect this to an output file for further viewing. This will take a while to run
Now open the file in sublime Now we can see the code in better, notice lots of javascript specific functionality, lots of forwards and backwards . The function has 419 lines of javascript which is quite meaty. This is the real beast behind the curtain, and even from this we can get an idea of what the attacker was planning and how the code is able to spin up so many processes and infect your HD. I am going to leave this tutorial here, as I will be focusing on my DevOps Automation series, but I thought this was important enough it was worth doing a flash tutorial on. If you wish to see more of this, then please reach out to me and I will prioritise the second part on further analysis.
Adam McMurchie 1/Sep/2017
